
Why Historical IP Reputation Matters More than Ever
Why Historical IP Reputation Matters More than Ever for Cyber Attack Prevention
Read More

Uncover your network's biggest threats with applied threat intelligence.
Packet sampling, traffic encryption, lack of focus on the outbound, misconfigurations, unmanaged devices. These are all common things that can cause a reduction in visibility.
To fully secure a network, you need to see all the comms that are happening.
Schedule a Demo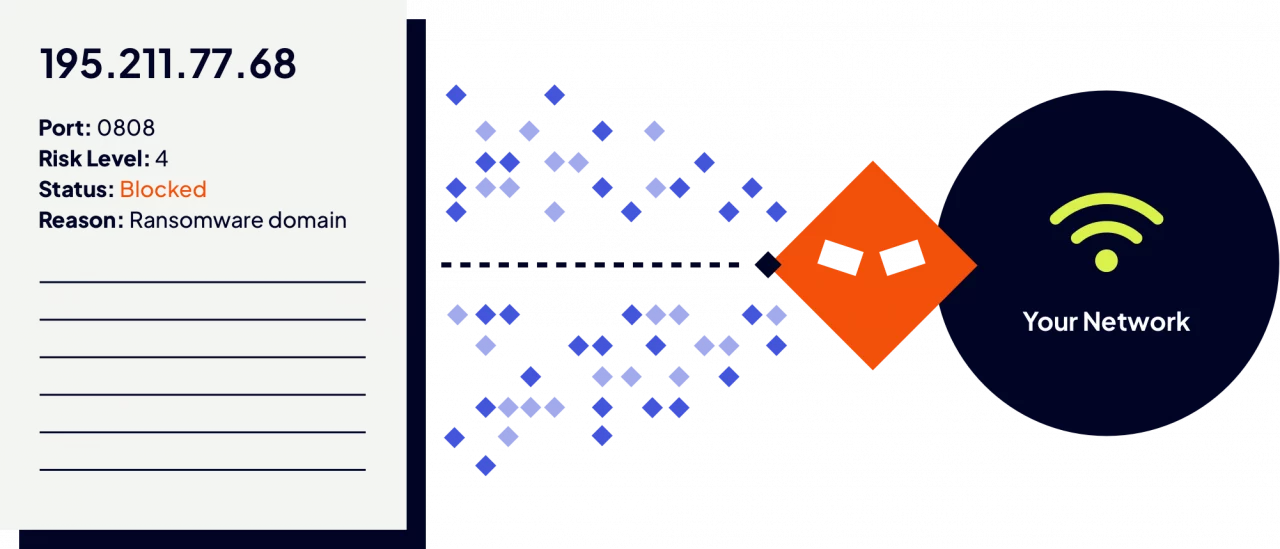
Enterprise-grade protection for your organization's most critical assets.
Your protection starts right when you turn it on. You can see every network communication sent and received. And with our applied threat intelligence, you'll know which comms are malicious and why.
Explore Applied Threat IntelligenceExpose all your inbound and outbound network communications including those from unmanaged, unpatched, and outdated devices that can't handle software updates.
Get real-time insights from cyber intelligence trusted by the U.S. government.
Intrusion's applied threat intelligence integrates into your existing architecture with little to no changes in infrastructure.
Compared to traditional threat intelligence models, applied threat intelligence will save you money and can help you scale.
Trusted by enterprises and government agencies for over three decades of cybersecurity excellence.
Monitor inbound and outbound traffic with Shield, Intrusion's on-premise threat hunting device. Powered by our Global Threat Engine, Shield automatically identifies malicious or unknown connections.
Learn More

Cloud provider security is not enough. Upgrade your cloud security with Shield Cloud, a dynamic gateway between your virtual private cloud (VPC) and the public internet.
Learn MoreReduce risk exposure and harden your ever-expanding network surface. Shield Endpoint enables remote connectivity from any device, anywhere in the world.
Learn More

Let Intrusion help you protect your most valuable assets. We have been in the networking and threat hunting business for over 30 years. Our threat consulting team provides in-depth insights into what's happening on your network.
Learn MoreAnswer 3 quick questions to get a personalized risk assessment and see how Intrusion can help protect you.
See what our customers say about protecting their networks with Intrusion.
Intrusion detected threats that our existing SIEM completely missed. Within the first week, we identified and blocked over 200 malicious connections we had no idea existed.
The applied threat intelligence approach is a game-changer. No more waiting for signatures or updates - we're protected against zero-day threats from day one.
After implementing Shield, our incident response time dropped from hours to seconds. The visibility into our network traffic is unprecedented.
Stay informed with the latest cybersecurity insights and threat intelligence.

Why Historical IP Reputation Matters More than Ever for Cyber Attack Prevention
Read More
Indicators of Compromise: What They Are and How to Identify Them
Read More
How IP Address Reputation Informs Network Security
Read More

Schedule a personalized demo and see how Intrusion can protect your organization.
Protecting networks and securing digital assets for over 30 years.